Replaying Beacons with the AirPcap Nx
The company I work for makes a Wi-Fi scanner, and while I think that it does a really good job of interpreting 802.11 beacons and probe responses, every now and then a customer finds a little bug, or at least a weird beacon from an access point or SOHO wireless router.
For a long time, I wished that I had a way to replay those beacons to see how our Wi-Fi scanner would interpret them, firsthand. Today, I had an epiphany. I have an AirPcap Nx, which in addition to being a packet capture device is also a packet injection tool!
If you have a PCAP file containing beacons, you can easily replay them with the AirPcap Nx. Here's how to do it:
1. Open the PCAP file in Wireshark.
2. Select the beacon that you wish to replay by clicking on it.
3. Save the selected beacon off to a new file in File > Export Specified Packet with the Selected Packet option.
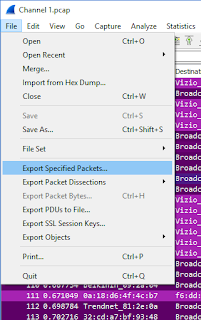
4. Open AirPcapReplay.
5. Set the Transmit Mode to User-defined Packet Period, check Respect Packet Channel, and check Respect Packet Rate.
6. Set the Packet Period to 104 milliseconds, and the number of File Transmissions to 500 or so.
Note: I like to set a finite amount of packets to inject, as I've noticed that I can't always click the Stop button and have to force close AirPcapReplay. Setting a finite amount of packets resolves this problem.

7. Click Transmit.
That's it! You should now see whatever beacon from the capture file being replayed from the AirPcap Nx, which in turn will be detected by any clients who are in range and listening:

For a long time, I wished that I had a way to replay those beacons to see how our Wi-Fi scanner would interpret them, firsthand. Today, I had an epiphany. I have an AirPcap Nx, which in addition to being a packet capture device is also a packet injection tool!
If you have a PCAP file containing beacons, you can easily replay them with the AirPcap Nx. Here's how to do it:
1. Open the PCAP file in Wireshark.
2. Select the beacon that you wish to replay by clicking on it.
3. Save the selected beacon off to a new file in File > Export Specified Packet with the Selected Packet option.
4. Open AirPcapReplay.
5. Set the Transmit Mode to User-defined Packet Period, check Respect Packet Channel, and check Respect Packet Rate.
6. Set the Packet Period to 104 milliseconds, and the number of File Transmissions to 500 or so.
Note: I like to set a finite amount of packets to inject, as I've noticed that I can't always click the Stop button and have to force close AirPcapReplay. Setting a finite amount of packets resolves this problem.
7. Click Transmit.
That's it! You should now see whatever beacon from the capture file being replayed from the AirPcap Nx, which in turn will be detected by any clients who are in range and listening:

This comment has been removed by a blog administrator.
ReplyDelete